
Authentication is one of those topics that we get quite a few questions about. And we can see why. It's a big, complex topic, and even within Weaviate, there are many options available which can make it seem quite confusing.
The core concept of authentication is relatively simple. When a client (e.g. a Weaviate client) sends a request to a server (e.g. a Weaviate database), it includes a "secret" that provides some assurances to Weaviate as to who that request is coming from, so that it can operate on that information.
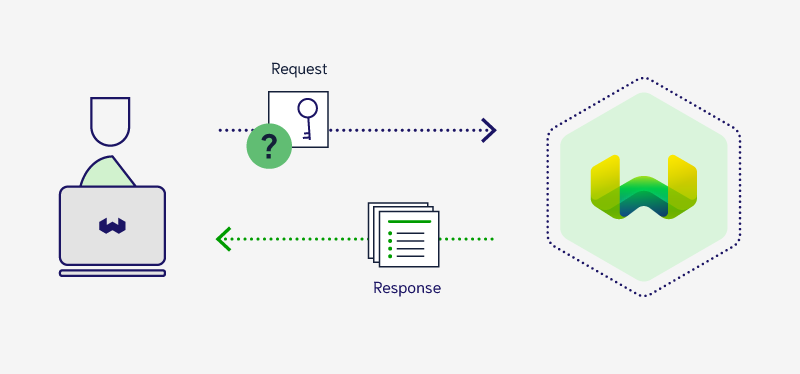
In other words, the server can provide as much access as the particular user is allowed.
But balancing security with usability can be a tricky line to draw, as everybody has different needs and often use different systems.
So, we thought that this might be a good time to provide an overview of all things authentication in Weaviate. Also, we've recently introduced an API key-based authentication method, which we think might be a good balance of security and usability for many of you. Please check them out below.
We would love to know what you think of video content. Would you like to see more of them? Are there any particular types of videos you'd like more of?
Please let us know below or on YouTube, and we'll do our best to listen. 😁
Videos
Introduction to authentication in Weaviate
Timestamps
- 0:00 Overview
- 0:13 What is authentication? & Key considerations
- 0:58 Overview of available authentication options in Weaviate (anonymous / API key authentication / OIDC authentication)
- 1:54 General Recommendations
Authentication: A client-side perspective
Timestamps
- 0:00 Overview
- 0:28 Getting authentication information from Weaviate Cloud
- 2:10 Authenticating against Weaviate
- 2:28 Anonymous access
- 3:01 API key authentication
- 3:45 OIDC (username+password) authentication
- 4:21 Read-only key
- 4:38 Authentication in action
- 5:36 Wrap-up
Authentication: Key concepts
Timestamps
- 0:00 Overview
- 0:31 Anonymous access
- 0:46 Authentication
- 0:58 API key authentication
- 1:04 OIDC authentication
- 1:36 Authentication & Authorization
- 1:52 A comparison of options
- 2:09 Additional complexities in OIDC
- 2:54 summary
Authentication: A server-side perspective
Timestamps
- 0:00 Overview
- 0:35 Weaviate without authentication
- 1:39 Setting up API key access
- 2:32 Enabling authorization (tiered access)
- 3:46 Setting up OIDC access
- 5:30 Enabling authorization with OIDC
- 5:54 Summary
- 6:02 Relevant environment variables
Read more:
- How to configure authentication
- How to configure authorization
- References: Environment variables
- Weaviate clients
Ready to start building?
Check out the Quickstart tutorial, or build amazing apps with a free trial of Weaviate Cloud (WCD).
Don't want to miss another blog post?
Sign up for our bi-weekly newsletter to stay updated!
By submitting, I agree to the Terms of Service and Privacy Policy.
